Easy-Data Computer Geek v.1.0

Introduction
This is a tool that wasnt ment to be! I run a multimedia site and this tool has nothing to do with multimedia, still, here it is. The reason for this tool is just that I did need several of the tools inside this program my self to fix some problems i had, and as usual I rather create my own instead of using others. The fact that the old Easy-Data also was a network and security site, and that I am an old school hacker (white hat) makes it a little bit easyer to understand why a tool like this is released by me. Another reason is that I am a bit tired/bored with the painful job it is to rewrite the whole EDM 2013, so creating this tool was really fun for a change.
The Computer Geek program is not a tool for ordinary computer users, rather for the more experienced users like system administrators etc. And obviously for all the geeks out there :-) That said, there are parts of this program that should fit most computer users, but also a few tools that requires knowledge. Like the ADS tool, and the Portscanner tool. ADS can be used for malicious purposes, and can absolutely f***k up your system in worst case. On the other hand the ADS scanner can help you find malicious code/software on your computer that far from all antivirus tools can. Regarding the Portscanner. This tool is not dangerous to use, but the moment you try scanning computers on the internet things can go wrong. It is not legal to do portscans in several countries. Norway is one of them. I have personally been kicked out by my ISP reasoned a portscan i did for a norwegian newspaper a few years ago. Even if we told them before we started scanning that this was just a test.
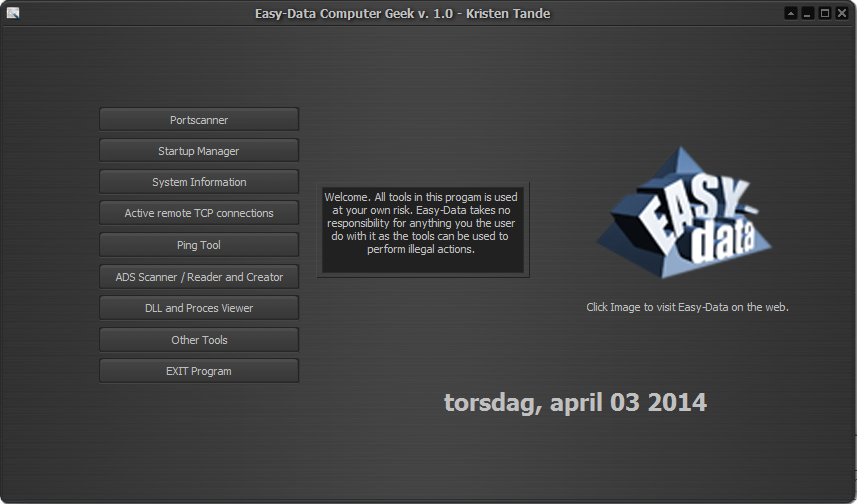
A quick overview of the tools inside
The first tool in the list is the Portsanner. This tool is used to scan for open ports on a computer.
PORT SCANNING
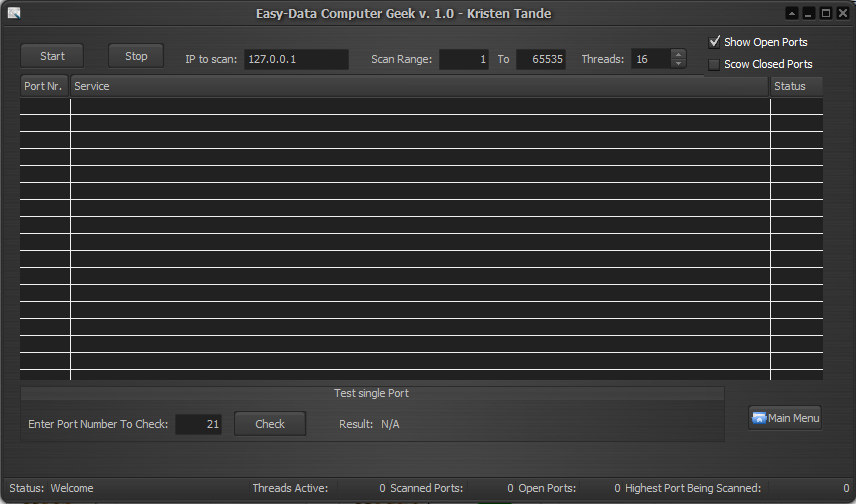
Port Scanning is the name for the technique used to identify open ports and services available on a network host. It is sometimes utilized by security technicians to audit computers for vulnerabilities, however, it is also used by hackers to target victims. It can be used to send requests to connect to the targeted computers, and then keep track of the ports which appear to be opened, or those that respond to the request. This portscanner has not an option for port sweeping as it is not ment to be used as a hacker tool. It is a fast threaded scanner that also shows information on most of the ports on a computer. That said, there is 65535 ports on a computer, so I do not have info on all the ports, but it will be updated often until the list is complete.
IS PORTSCANNING LEGAL?
Port scanning is like ringing the doorbell to see whether someone's at home. The police usually can't do anything about it. They have to wait until a crime is committed. For example, in Germany and Singapore, port scanning cannot be prosecuted. However, consult your local lawyer to see if this is true in your country. Sometimes, if a computer system is affected too much by a port scan, one can argue that the port scan was, in fact, a denial-of-service (DoS) attack, which is usually an offense. Scanning your own computers is 100% legal and it is also a good idea to check your computer regulary for security measures.
STARTUP MANAGER
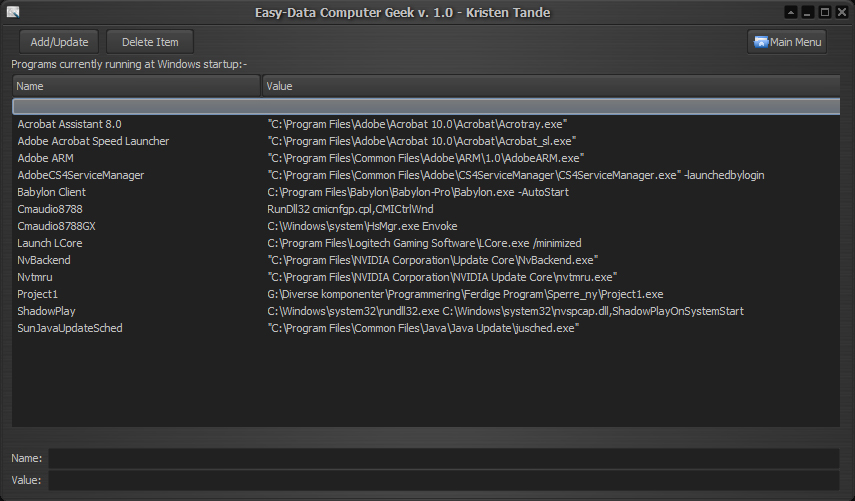
The second tool is the Startup Manager. This is a tool where you can manage wich applications that should start automaticly with Windows. First, note that you should be concerned with *all* programs that start automatically, not just with those that go into the system tray. Not all autostarting programs manifest themselves by an icon in the tray. Also remember that all applications running use system resources, so dont add it if you really dont need it!
Useful reading:
A list of possible autostart methods in windows
SYSTEM INFORMATION
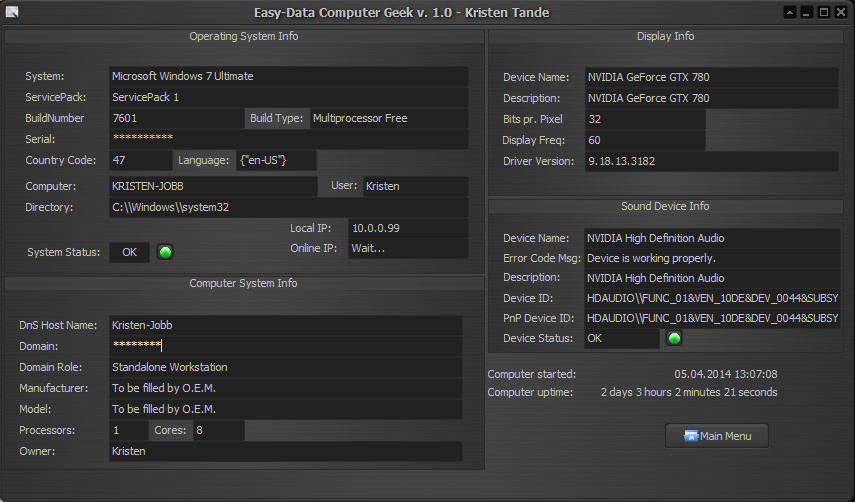
This is not a tool, just a quick method of getting information about your system. Nothing fancy, but you will be notified if the tool find any errors in the system. As long the lights are green everything is ok. That goes for the system status, and the main sound device.
ACTIVE REMOTE TCP CONNECTIONS
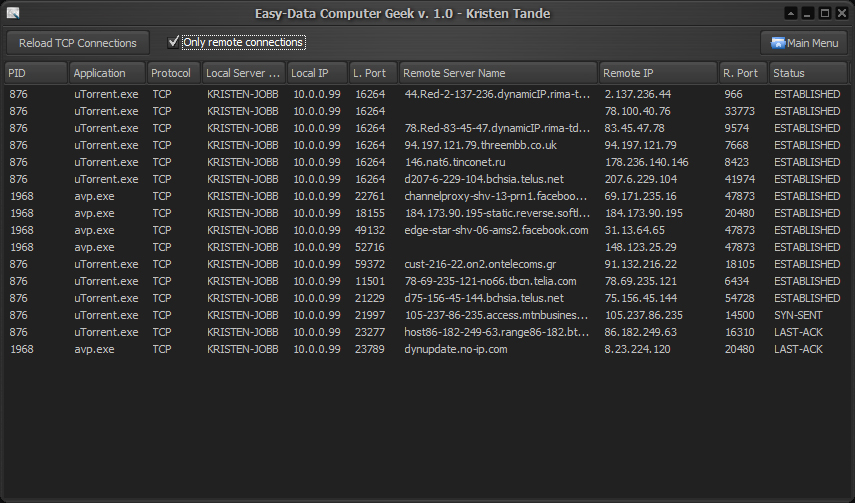
This tool does exactly what it says in the title. It will show all active connections your computer has to the outside world. It is kind of like the dos command Netstat, but more advanced as it will show more information.
THE PING TOOL
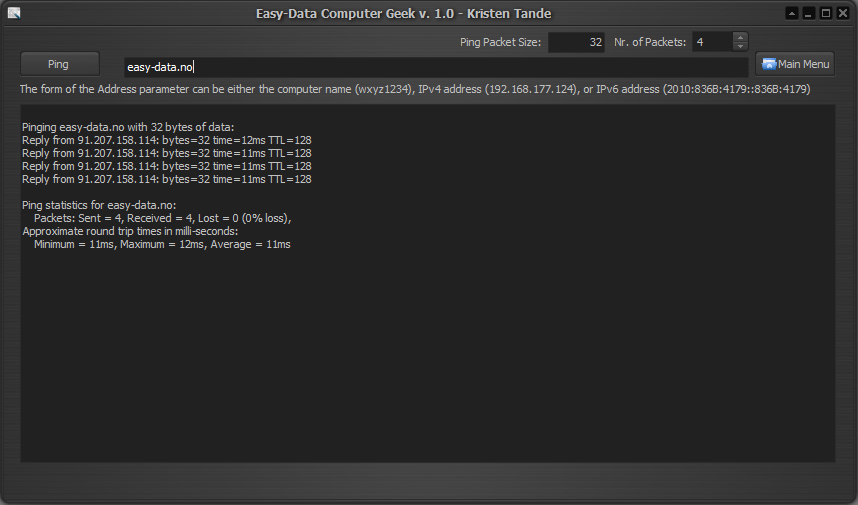
Ping is a computer network administration utility used to test the reachability of a host on an Internet Protocol (IP) network and to measure the round-trip time for messages sent from the originating host to a destination computer. The name comes from active sonar terminology which sends a pulse of sound and listens for the echo to detect objects underwater.
Ping operates by sending Internet Control Message Protocol (ICMP) echo request packets to the target host and waiting for an ICMP response. In the process it measures the time from transmission to reception (round-trip time) and records any packet loss. The results of the test are printed in the form of a statistical summary of the response packets received, including the minimum, maximum, and the mean round-trip times, and sometimes the standard deviation of the mean.
THE ADS SCANNER TOOL
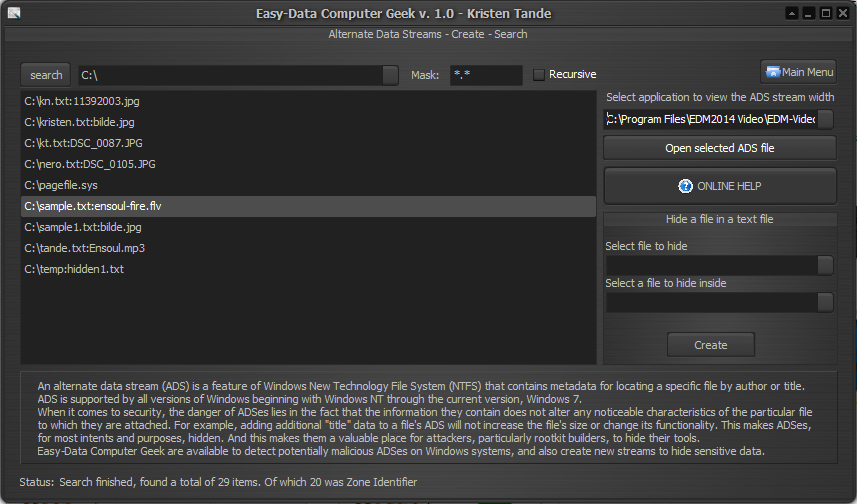
Anyone who is in the security arena should know about Windows Alternate Data Streams, otherwise known as ADS. Though not highly publicized, lack of this little known attribute of the Windows NTFS file system may affect how you solve a problem in the future.
ADS were introduced into the Windows NTFS file system starting in Windows NT 3.1. This "feature" was implemented in order to allow compatibility with the Macintosh Hierarchical File System (HFS). In brief, the Macintosh file system stores its data in two parts, the resource fork and the data fork. The data fork is where the data is actually contained and the resource fork is used to tell the operating system how to use the data portion. Windows does a similar thing through extensions such as .bat, .exe, .txt, .html. These extensions tell the operating system how to use the particular data found in the files.
For windows to be compatible with the Macintosh file system, they introduced alternate data streams. This hidden stream is used as the resource fork was used; to tell the system how to use the data contained in the file.
There are several documents explaining the possible danger of ADS. as the following articles will show you.
Windows NTFS Alternate Data Streams - Symantech
There are numerous applications including Windows which internally use alternate data streams for various purposes. Here are some of the well known streams....
- SummaryInformation
This stream is created by Windows when user updates the summary information for the file. - DocumentSummaryInformation
This stream is created by Windows when user updates the summary information for the file. - {4c8cc155-6c1e-11d1-8e41-00c04fb9386d}
This is stream with zero size created by Windows when user updates the summary information for the file. - Zone.Identifier
This is another well known stream created by Internet Explorer for every downloaded file. It is basically text stream with size normally less than 50 bytes. (Computer Geek does not list these streams by purpose) - encryptable
This is a stream with zero size attached to the file 'Thumbs.db'. - favicon
This is icon stream attached to the favorite links stored by Internet Explorer. - AFP_AfpInfo
This is stream of icon type belongs to Macintosh system.
In addition to legitimate programs, it is also being used by malicious Rootkit programs such as Mailbot.AZ, Trojan.Win32.Agent.alt etc to hide their drivers.
Easy-Data Computer Geek does not report Zone.Identifier streams as it filter them out as not dangerous. In addition to finding, you can create ADS streams with this tool. This version of the tool does not allow users to delete such streams, but fortunately there is a pretty easy way of cleaning them. ADS dos only work with NTFS partitions, not FAT. So if you find a file you want to clean, just copy it to a FAT formated disk. You will get a windows that pops up that asks you to confirm stream lost, just click yes. When you do so the ADS part will not be able to follow the file, then delete the original file on the NTFS disk and copy back the cleansed file from the FAT formated disk.
Another way to manually delete is to rename the file and then use the "type" command to pipe it back to the original file name.
Example:
C:\>ren sample.txt delme.txt
C:\>type delme.txt>sample.txt
C:\>del delme.txt
Another good thing is that ADS streams will not follow the file if uploaded to the internet, or by emailing a file, but it will be intact when copied between computers in a LAN (as long as the reciever disk is NTFS.)
To be updated.....
THE DLL AND PROCESS VIEWER
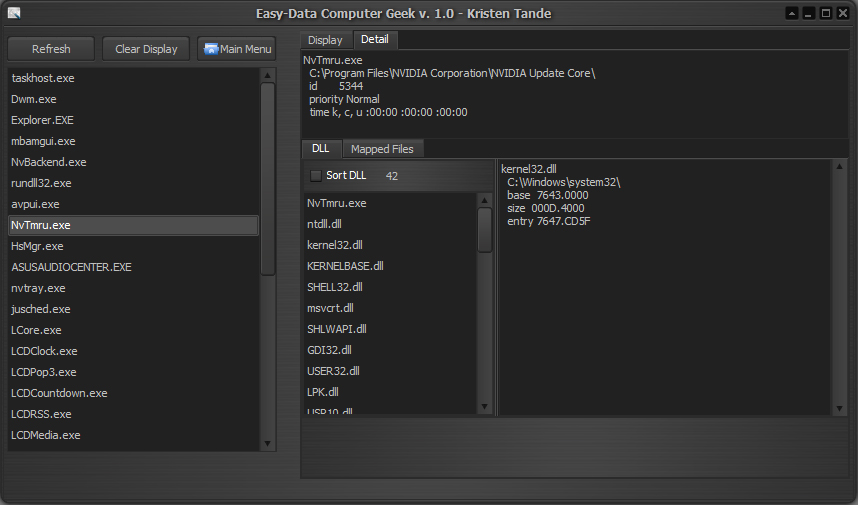
This tool shows a tree of all running process, the modules that each one is using, and the resources contained in each module.
OTHER TOOLS
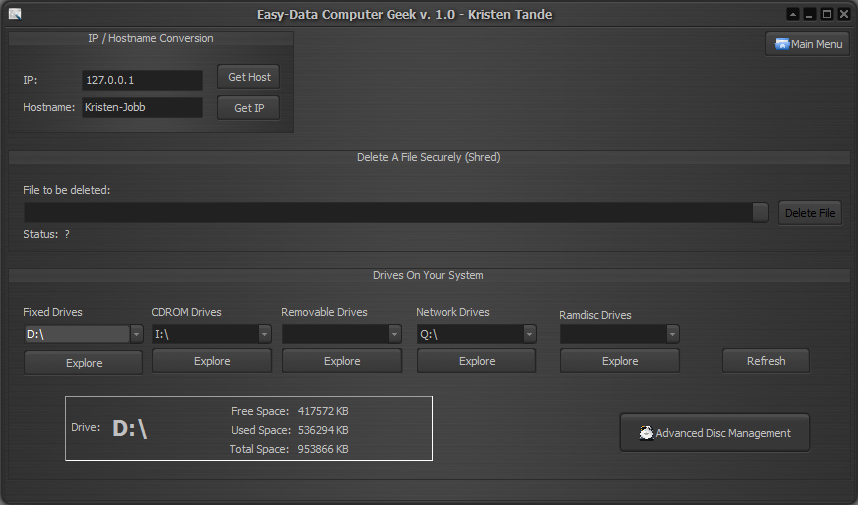
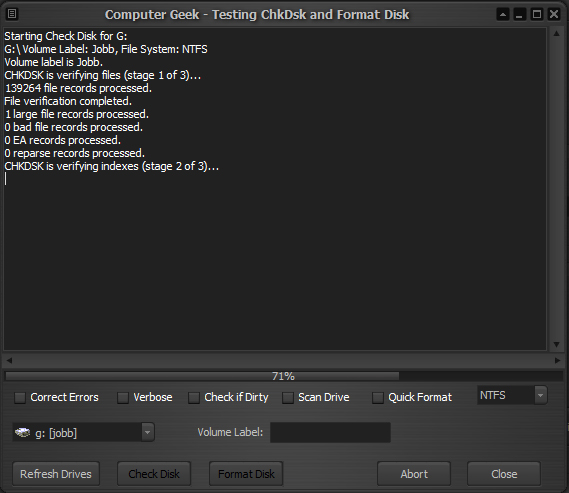
Her you will find a few tools that may be of use. There is a IP/Hostname Convertion tool, a secure file delete tool (file shredder), and a view of all disk drives available on your system listed by drive type. Finally a disk management tool where you can check a disk for errors, format disks etc.
SUMMARY
This application will be updated with new features whenever I have some time to do so, but the multimedia tools will always come first. Any suggestions on future versions is welcome. Several of the tools in current version is buildt upon samples made by other found around the net, and reasoned this, I recommend you to be careful when using it. That said, I have done quite a lot of testing, and have not had any trouble. So as far as I can see all current tools are safe. Anyway, look at Computer Geek v. 1.0 as a beta version.






